- Solutions
- Solutions
- Home Health
- Hospice
- Life Plan Community
- Palliative Care
- Private Duty
- Senior Living
- Skilled Nursing
- Skilled Nursing
- Skilled Nursing Software
- Advanced Insights
- Customer relationship management
- Data and analytics
- Financial & operations management
- Marketing
- Nutrition management
- Referral management
- Regulatory compliance
- Retail management
- Resident engagement
- Revenue cycle management
- Skilled nursing interoperability
- Partners
- Blogs
- Resources
- About
- User Conference

New Year, New Phishing Attempts
Just recently, Marriot Hotels announced that they were affected by a data breach and over 500 million hotel guests had their data exposed. It is much easier to trick someone into giving a password than it is to brute force or guess it. It’s much easier to trick someone into doing something they shouldn’t than to compromise a system and write code. The present technology is capable of combating a lot of threats and does a decent job filtering out a lot of noise. However, the last line of defense is always people– that’s you.
Below are some quick tips for identifying scams. This is not an exhaustive list but meant to be a quick refresher.
- The email is asking you for your credentials or telling you that you have an overdue invoice. No one is going to ask you for your credentials via email. If you have an overdue invoice don’t follow the email – Call the company’s collections department directory.
- The spelling and grammar are usually (but not always) terrible. A large percentage of scams originate outside the United States by non-English speakers. The bulk of the emails are run through a translator and it shows.
- The email display name might look familiar, but the originating email address is not correct. When you open the email message look at the sender information – it will be in the format “Display Name <email address>”. If the actual address does not match, its surely a scam.
- The email is nothing more than an invitation to check out some link or download some document. If you were not explicitly expecting a document or a reference to an external link then don’t open it or follow the link. Reach out to the person (not via email) and ask if it’s questionable.
- If you follow a link, look at the browser address bar to ensure you are where you think you are. The browser should display the URL of the page you are at, which should match the expected destination (ie. DocuSign documents should be at *.docusign.com).
- Never execute any downloaded files unless you are 100% sure you know what they are. If you download something and try to run it, never enable macros unless you are 100% certain. Never blindly give it permission to run. If you have a question– Ask, don’t take the chance.
- Use common sense. It’s highly unlikely that anyone is going to email you asking for a money order or to purchase iTunes gift cards. If they do, confirm with them in person or via phone call and get a second opinion before doing anything.
At the end of the day-use common sense and ask yourself if you should do something. Does it make sense for your job? Are you expecting something? Can you reach out to the person via a method other than email? What is the worst that happens if you DON’T open the email or follow the link?
Frequently Asked Questions:
“Hey Nick, those are pretty generic tips– how do I actually do those things?”
How do I check the sending email address?
When you open an email message in Microsoft Outlook (either using the Reading Pane or not) the first information displayed in the upper left-hand corner will display the sender’s name and the sender’s address.
In the example below the Sender’s Name is highlighted in yellow and the Sender’s Email is circled in red.

- Spoofing a senders name is easy, the attacker just sets their name to match.
- Spoofing a senders email address is also easy. However, most mail systems will identify when an email address is spoofed and send this to either your trash or your junk mail and display a banner warning that the message is fraudulent.
How do I check the URL in the browser?
- The first line of information in all modern browsers is the Address Bar and contains the URL. It should be in the form of http://<some_address_here> or http://<some_address_here>.
The most important part of the URL to quickly review is the Domain Name.

- It is important to note that the use of HTTPS (or a green SSL check) does NOT mean you are safe and secure. All this indicates is that you have an encrypted tunnel to that site. It could still be a bad site. Thanks to organizations like “Let’s Encrypt™” it’s trivial to get SSL Certificates for malicious sites.
- When you are looking at the URL you want to ensure that the Domain and Top-Level Domain are where you want to be. If you are logging into something Microsoft (Office 365) related this should always be Microsoft.com.
- Be advised that while less common these days, some sneaky attackers use letter replacement techniques or misspellings to trick you into thinking you are at the right spot. An example would be M1crosoft.com (notice the 1 instead of the i).
- Be advised that some sneaky attackers use a different Top Level Domain (TLD) to trick you into thinking you are at the right spot. An example would be Microsoft.gz or Microsoft.biz.
Examples of Scams
Example 1: Fake link using someone I know
The email below arrived in my Junk mail and was intended to look like my sister-in-law wanted me to check something out. The scammer used her name (1), likely pulled from my list of friends on Facebook with some other email (2) they either owned or compromised. The body of the message was nothing more than an attempt to get me to follow a link to check something out (3). The link (4) was obfuscated and pretty random looking. I would never follow this.

Example 2: Fake link using false pretense from known service
The email below arrived in my Junk mail and was intended to look like I received a DocuSign document. My first thought was “I am not expecting a document, thus I do not care”. Additionally, you can see that the Display Name (1) was set to look like it came from DocuSign, but the Email Address (2) was certainly not a DocuSign address because it came from “@jeffhartmd.com”, which was likely a compromised account. Further, you can see that there is a link to “See Invoice” (3) but if I hover over the link to look at the actual URL it is most certainly not DocuSign (4).

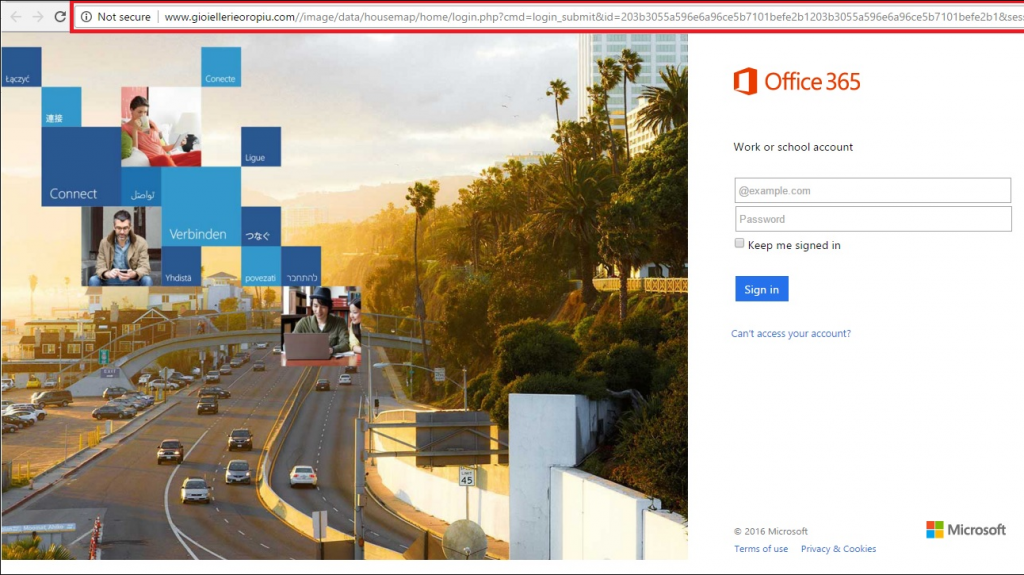
Example 3: Fake site to harvest credentials
The example below is a replication of the Office 365 login page. By examining the URL in this image you can clearly see that it is NOT https://login.microsoft.com but instead a clever fake to fool you into entering your Office 365 credentials.
A couple of important things to note here:
- Always check the URL and ensure you are in the right place. It’s trivially easy to exactly match the visual layout of someone else’s page (as evidenced here).
- Most company’s login pages are branded. As soon as you enter your Username, the Logo will change to your company’s logo. Fake pages will almost always still have the generic Office 365 logo.
- If you are fooled by this page and enter your credentials, clicking the Sign In page then does two things:
- It records the username and password that you just entered into the attacker’s database.
- It REDIRECTS your browser to the correct login page. This makes you think you just entered your credential wrong. The second time, since you are at the correct place now, you are logged in and think nothing bad happened – but you are now compromised.
- Given the above, pay close attention to the URL BEFORE you enter any credentials.
- Please also be aware that you don’t need to actually click ‘Sign In’ to lose your credentials. Simply typing them into the field could be enough.
 Check out other MatrixCare articles on phishing to learn more helpful tips:
Check out other MatrixCare articles on phishing to learn more helpful tips:
‘Phishing – It’s A Jungle Out There!’ https://www.matrixcare.com/blog/phishing-its-a-jungle-out-there/
‘What’s the Difference Between a Terrible Password and a Great Password?’ https://www.matrixcare.com/blog/terrible-password-vs-great-password/
Request a demo today for a closer look at MatrixCare.
See what MatrixCare can do for you
Nick Sykes
Senior Director, Information Technology at MatrixCare
Related Posts




See MatrixCare in action
Start by having a call with one of our experts to see our platform in action.
MatrixCare offers industry-leading software solutions. Thousands of facility-based and home-based care organizations trust us to help them improve efficiency and provide exceptional care.




